Topic: Security
-
We released a new course for our SQLBI+ subscribers: Security in Tabular Semantic Models. This course explains how to implement security in Tabular semantic models, considering different requirements, data model design, DAX implementation, and performance. The training is reference material… Read more
-
How to implement security in Tabular semantic models considering different requirements, data model design, DAX implementation, and performance. Read more
-
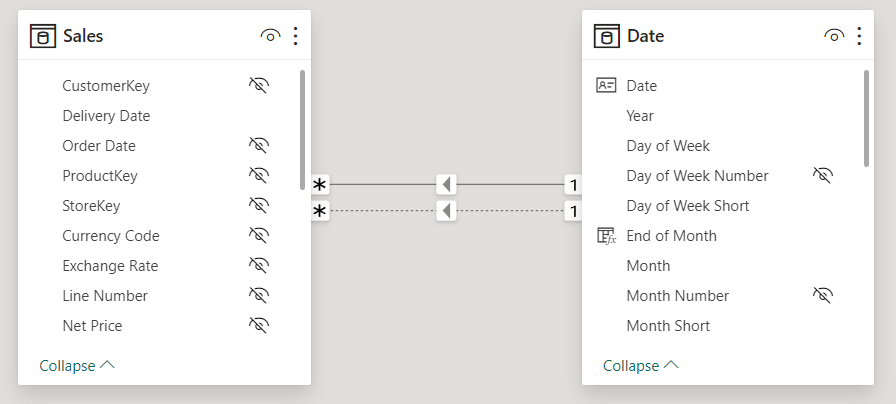
When you apply row-level security to a semantic model, there are limitations in using the USERELATIONSHIP function. This article shows the issues, provides a workaround, and its restrictions. Read more
-
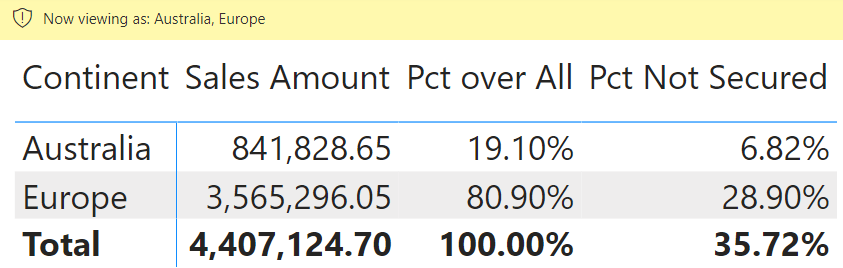
This article shows how to compute ratios when row-level security hides some of the data. If the percentage also includes the hidden rows in the comparison, you should customize the data model and the measures involved to get the right… Read more
-
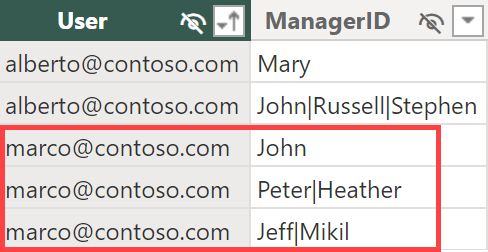
How to apply dynamic security roles in a hierarchical organization to minimize the maintenance effort on the security configuration and obtain the best performance at query time. Watch now
-
This article describes how to apply dynamic security roles in a hierarchical organization to minimize the maintenance effort on the security configuration and obtain the best performance at query time. Read more
-
This article describes how to read the active security roles in a Tabular model for Power BI or Analysis Services. This way, you can use measures and calculation groups to customize a report based dynamically on security roles active for… Read more
-
This article describes how to hide measures from a group of users by leveraging object-level security in Power BI and Analysis Services. Read more
-
When you create and publish a composite model using DirectQuery for Power BI datasets and Analysis Services, you should pay attention to the minimal permissions required to consume data. For example, consider the following scenario: Base is a shared dataset… Read more
-
Explore how you can hide columns and tables to Power BI users by using the Object Level Security (OLS) feature released in February 2021. By hiding objects, you also hide derived calculations like measures, calculated columns, and calculated tables. The… Watch now